If you have been in the cyber world for any time at all you have probably received an email from a man eight countries away from you, seeking to give you riches beyond your imagination because he has no living heir to give his wealth to…

We’ve touched on this before in several past blog posts: How to Recognize Email Scams, How backups protect you from hackers, and also in our post that talks about Nate’s book: The Cyber Security Guide.
The scenario might look something like this: “I am on my death bed and have lived a grand life. However, I never married and have no children to leave my estate to. I have selected you to take on my 4.2-billion-dollar estate. Please send me your bank account number and $5,000 (for transfer costs) and you will receive my estate within a week.”
Of course, the week goes by, the money never comes, the victim is out $5,000, and now has given personal bank information to a hacker on the internet. This used to be one of the more common ways people would find their information breached. This is what we in the tech field like to call: phishing. Phishing is the practice of sending fake emails to convince individuals to reveal personal information such as passwords and credit card numbers. Phishers pretend to be from reputable companies, so the readers are tricked into trusting them.
Phishing is the oldest trick in the book. However, people began to catch on to these scams, so they’ve become less and less effective as time has gone by.
30% of phishing emails are opened by users, and 12% of these targeted users click on the malicious link or attachment. -Meharchandani, D. (2020, December 7). Staggering Phishing Statistics in 2020. Security Boulevard. https://securityboulevard.com/2020/12/staggering-phishing-statistics-in-2020/
With only 12% of the users clicking and downloading the malware, we see that it’s not as frequent as it could be. Hackers now need to create different types of cyber attacks to trick people into giving out information. So, it’s time to say, “So long,” to foreign benefactors in another country, and say, “Hello,” to small, everyday scams that people might just fall for. I am talking about smishing. Smishing is a new form of phishing in the world of cyber crimes. To access private accounts or businesses, a scammer will try to get personal information from a user through a text or SMS message. It is a practice that is becoming more and more prevalent.
Smishing steps out of the bounds of phishing and attacks us on a front we tend to have a little more leniency toward. Communicating through text messages is an effective way to get goals accomplished quickly. We text our banks, we use texts for our two-factor authentication, we use Apple Pay at the grocery store, and Amazon is always a convenient click away. With all these access points available to us, our most vital privacies are sitting and just waiting to be stolen by one strategically placed text message.
We are often quick to trust a text message that claims to be from our bank, letting us know our paycheck just deposited, or that a bill just got pulled from our account. It’s very easy for us to disregard a seemingly harmless message. And that is exactly what clever hackers are hoping for.
Smishing uses elements of social engineering to get you to share your personal information. This tactic leverages your trust in order to obtain your information. The information a smisher is looking for can be anything from an online password to your Social Security Number to your credit card information. Once the smisher has that they can often start applying for new credit in your name. That’s where you’re really going to start running into problems.
Another option used by smisher is to say that if you don’t click a link and enter your personal information that you’re going to be charged per day for use of a service. If you haven’t signed up for the service, ignore the message. If you see any unauthorized charges on your credit card or debit card statement, take it up with your bank. They’ll be on your side. What Is Smishing? (2018, January 18). Norton Security. https://us.norton.com/internetsecurity-emerging-threats-what-is-smishing.html
One carefully placed text message from a hacker posing as your bank account or Amazon could have you sending your password and login information, or clicking a link downloading malware or ransomware, to your device.
One of the paradoxes of this kind of attack is that the smishers play on your fears of hacking in order to hack your account. They’ll send you text messages claiming to be from your bank, “warning” you about a large transfer or a new payee added, and giving you a number to call or a link to click on to block this potentially unauthorized access to your account. In reality, of course, the transfer or new payee doesn’t exist; the link sends you to a spoofed website that looks like your bank’s and asks for your username and password, and the phone number connects you to the scam artists, who will try to wheedle the same sort of information out of you. Once they’re armed with those credentials, they can log into your bank account and plunder it. Fruhlinger, J. (2020, May 1). What is smishing? How phishing via text message works. CSO Online. https://www.google.ca/amp/s/www.csoonline.com/article/3538831/what-is-smishing-how-phishing-via-text-message-works.amp.html
If a smisher is able to get you to believe they are who they say they are, they can quickly disable a personal bank account or company within a few hours.
Bank smishing is often successful for a couple of reasons. One is that many banks really do have services that text you about suspicious activity on your account. An important thing to keep in mind is that legitimate messages should contain information proving that the bank already knows who you are: they might include the last few digits of your credit card or bank account number, for instance. Vague references to “your account” without any details should be viewed with suspicion. – Fruhlinger, J. (2020b, May 1). What is smishing? How phishing via text message works. CSO Online. https://www.csoonline.com/article/3538831/what-is-smishing-how-phishing-via-text-message-works.html
How did they get my number?
Well, there are many different ways this can happen. Social media outlets are known for selling data and information to advertisers. Once advertisers have your information, there is really no way to know where your information may end up after that. Especially if that advertiser has experienced a data breach. By now, anyone could have your info.
Their responses, released Thursday, show that some companies record — and then resell — your screen names, web site addresses, interests, hometown and professional history, and how many friends or followers you have. ProPublica. (2020, February 15). Yes, Companies Are Harvesting – and Selling – Your Facebook Profile. https://www.propublica.org/article/yes-companies-are-harvesting-and-selling-your-social-media-profiles
If you have ever filled out a card in your local mall for a chance to win that fancy Ferrari, you’ve given your contact info away to be sold to more advertisers. However, automatic dialing companies are capable of dialing numbers over and over until they hit the jackpot. All of these are ways that spammers and advertisers are finding their way to your phone.
Here are a few examples of smishing text messages that I have received in just the last few days:
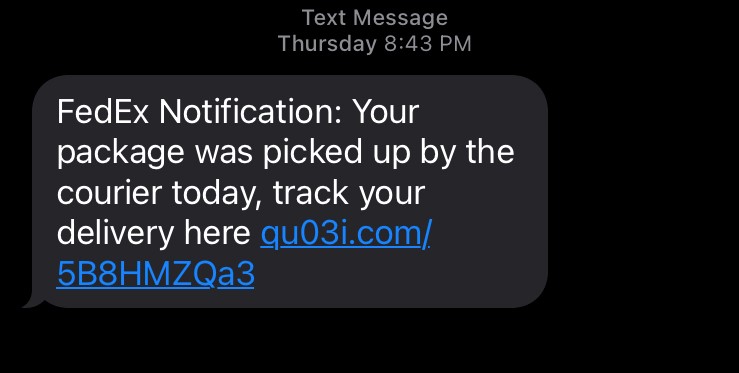
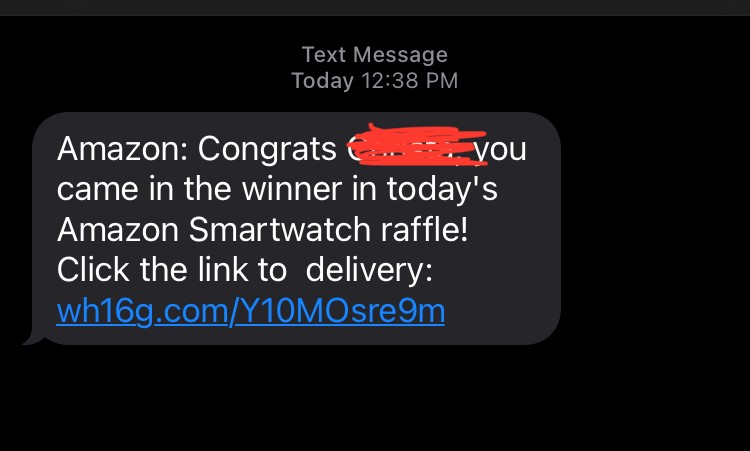
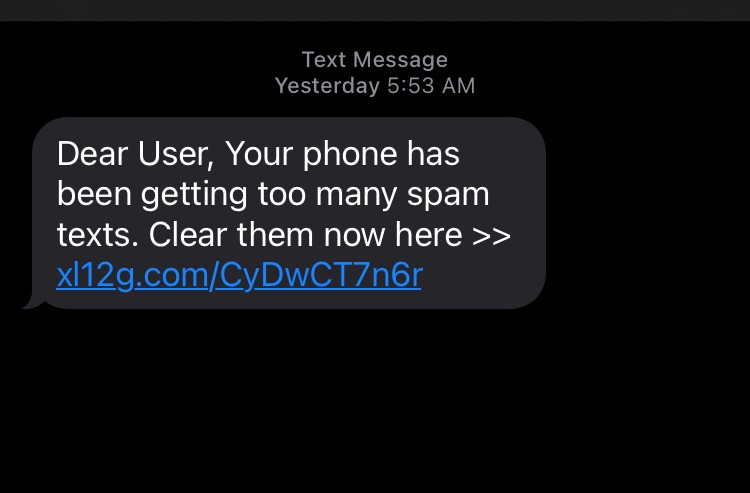
I must admit, that third one is my favorite. Scammers know just how frequently they are messaging you, so they try to convince you to click on a link to help you clear your phone from spam text messages. It’s quite a clever ploy. As you can see, they use several creative ways to tempt you into clicking their links. Being an avid Amazon user, I almost believed for a moment that I had possibly won a smart watch raffle. And with the amount of Fedex packages I receive, it would not be that unusual for me to receive a text message from them with updates for my package. However, Fedex and Amazon have direct avenues to track your packages. Always go directly to the website to find specific tracking on items.
This is a safe rule of thumb when it comes to any confirming of a smishing or phishing scam: Contact the business directly, call your bank directly, or if you receive a suspicious text or email from someone you were not expecting to hear from, contact them directly. Do not click any suspicious links.
Once your info is out there, it could end up anywhere, including being sold on the dark web. We did a post about the dark web awhile back – click here to read it. The dark web is a hidden side of the internet where scammers and hackers create, buy and sell malware, ransomware, and companies’/individuals’ private information. They have no issue using your info and then selling it on to the next guy.
If you’re getting spammed with text messages from people you don’t know, it’s likely because your number was lost in a data breach and then purchased on the dark web. Purchased on the dark web? Yes! Large swaths of data stolen consumer data get bought and stolen on dark web marketplaces, often for only a few dollars per download. From there, all a cybercriminal needs to do is set up an automated service to with a virtual number and begin spamming phone numbers with text message phishing attempts. Cook, S. (2020, November 2). What is smishing, and how can it be avoided? Comparitech. https://www.comparitech.com/blog/information-security/smishing/
How do I protect myself?
So, we now know what smishing is and how it happens. Now what do we do about it? Here are a few quick and easy responses for when you receive a text or email from a scammer.
1.Do NOT click the link.
2.Delete and block the messages.
3.You can forward the messages to 7726 (on your keypad, this spells S-P-A-M), and this will notify your carrier that the messages are spam. This helps your carrier report and track spam operations and prevents them from happening in the future. It also helps prevent continued scam attempts towards the user and other individuals in the future. The FTC (Federal Trade Commission) website also encourages users to report these messages directly to them by reporting the messages here.
Copy the message and forward it to 7726 (SPAM). How to Recognize and Report Spam Text Messages. (2021, January 22). Consumer Information. https://www.consumer.ftc.gov/articles/how-recognize-and-report-spam-text-messages
4.If you are not sure if the message is spam, look up the number online and see if it has been used in scams before.
5.Do NOT respond to the SMS.
If you want to take it a few steps further, you can report the calls or text messages to the FCC. The FCC has a complaints’ line built to prevent spam texts and robocalls.
Unwanted calls – including illegal and spoofed robocalls – are the FCC’s top consumer complaint and our top consumer protection priority. These include complaints from consumers whose numbers are being spoofed or whose calls are being mistakenly blocked or labeled as a possible scam call by a robocall blocking app or service. The FCC is committed to doing what we can to protect you from these unwelcome situations and is cracking down on illegal calls in a variety of ways: Stop Unwanted Robocalls and Texts. (2021, March 17). Federal Communications Commission. https://www.fcc.gov/consumers/guides/stop-unwanted-robocalls-and-texts
We know it is inevitable that we will be contacted by a spam call, email, or text message. Unfortunately, the avenues in which our data could be taken advantage of, are endless.
Maybe a Nigerian Prince will be reaching out to you soon to bestow millions-of-dollars into your bank account. Or maybe Amazon has picked you to be their new raffle winner for an IPad Air. Whichever approach a scammer will take to get your info, at least you now know how to be prepared.
Other solutions would be getting anti-malware software for your devices and keeping your devices and security settings consistently up-to-date. Make sure you are not using the same password on all your accounts and devices.
If you are a business, you might want to go a step further to secure your company and devices, including your employees’ work devices. A misplaced thumb tap could put ransomware into a company’s system. You can read our blog post about protection from ransomware takeovers here.
If you are looking for a way to create more security for your business, we can help you do that. Datacom Technologies has security plans to help keep all the back doors in your company closed and sealed from scammers and hackers. We would love to partner with you to find the best protection plan to fit your needs.
Click here to contact us through our website, or call us at 330.680.6002. Click here to buy your own copy of Nate Sheen’s book – The Cyber Security Guide.

